The New York Post suffered a hack Thursday morning that resulted in the newspaper posting several offensive headlines about US politicians, including racist remarks and calls for violence.
Users noticed something was off when the Post’s Twitter account pushed the obscene headlines, some of which were directed at New York politicians, to its 2.8 million followers.
In addition, the hacker managed to post(Opens in a new window) several fake headlines to the Post’s own website, which called for the death of President Biden, his son Hunter Biden, and Congresswoman Alexandria Ocasio-Cortez.
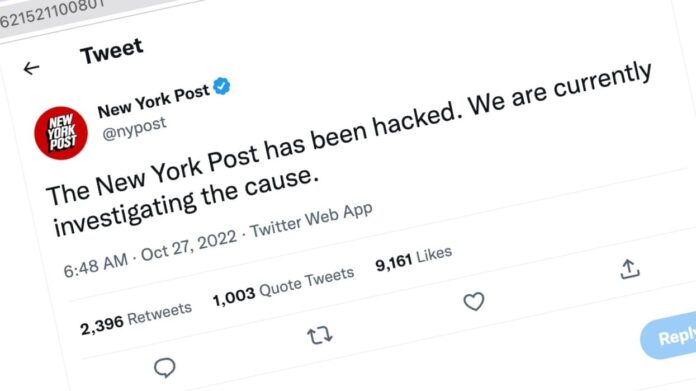
The newspaper later regained control of its Twitter account and posted(Opens in a new window): “The New York Post has been hacked. We are currently investigating the cause.” The offensive tweets and headlines have all since been removed.
A spokesperson for the newspaper told PCMag: “The New York Post’s investigation indicates that the unauthorized conduct was committed by an employee, and we are taking appropriate action. This morning, we immediately removed the vile and reprehensible content from our website and social media accounts.”
The employee, who has now been terminated, likely had access to the newspaper’s content management system, which can publish articles on the New York Post’s website and possibly to Twitter as well.
Recommended by Our Editors
The breach occurs a month after business magazine Fast Company suffered a similar hack, which involved the culprit gaining access to the media outlet’s content management system. The hacker then replaced Fast Company’s website with obscene headlines. In addition, the attacker also abused the push notification function for the magazine’s Apple News account to send out an offensive message to numerous iPhone users.
It remains unclear who pulled off the hijacking at Fast Company. But the hacker behind the breach apparently uploaded an article(Opens in a new window) to the magazine’s website, which alleged Fast Company had secured online access to its WordPress system with a default password “pizza123.”
Like What You’re Reading?
Sign up for SecurityWatch newsletter for our top privacy and security stories delivered right to your inbox.
This newsletter may contain advertising, deals, or affiliate links. Subscribing to a newsletter indicates your consent to our Terms of Use and Privacy Policy. You may unsubscribe from the newsletters at any time.
Hits: 0