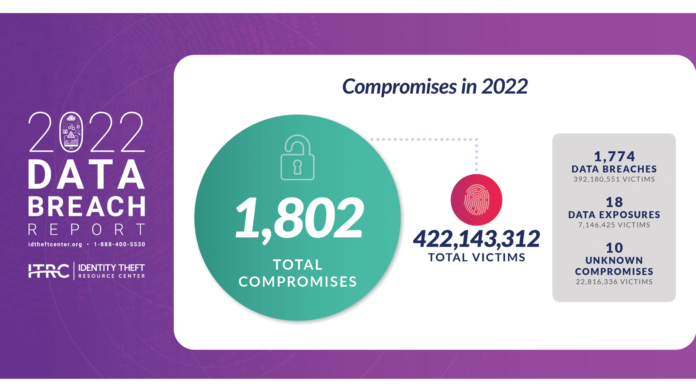
While 2021 was the year of the breach, 2022 wasn’t far behind. The 2022 Data Breach Report from the Identity Theft Resource Council (ITRC)—its 17th such report—indicates that we simply can’t trust our personally identifiable information (PII) with, well, anyone.
The good news is that slightly fewer breaches occurred from year to year—the number fell from 1,862 in 2021 to 1,802 for 2022. The bad news is that the number of victims in the 2022 breaches was much higher, hitting over 422 million (across full breaches and PII exposures), up from 294 million in 2021.
As you can see above, more than half of those victims were compromised by breaches at one company: Twitter makes the top 10 list twice. Had that not happened, the number of victims might have dropped 33% from 2021. (Twitter claims the bigger breach is bogus.)
The PII attributes stolen most frequently are names and Social Security numbers. And we’ve already written about the synthetic ID fraud that bad actors can perform with a SSN, even if they have no other information about you.
These 1,802 breaches took place in the US only, and are just those that were publicly reported; imagine what’s happening with your PII behind closed doors. Thankfully, many states, including Pennsylvania and Maryland, have new laws regarding companies’ responsibility to report breaches. Even so, there’s been an increasing lack of transparency—only 34% of the notices of a data breach include “victim and attack vector details,” according to the ITRC.
Recommended by Our Editors
Fewer breaches resulted from compromised cloud databases (75% fewer) and physical attacks, such as using stolen devices (down 46%). But there’s a reported increase in supply-chain attacks, in which the bad guys go after a company or entity that has stored or has access to the information for several other services.
For the full report, visit the ITRC(Opens in a new window); use its Notified(Opens in a new window) search and alert service to see whether your PII has been compromised. (The organization is working on a version for businesses, too.) Then read What to Do in the Aftermath of a Data Breach. You’re going to need it.
 4 easy things you can do to be more secure online — Clarification Please
4 easy things you can do to be more secure online — Clarification Please
Like What You’re Reading?
Sign up for SecurityWatch newsletter for our top privacy and security stories delivered right to your inbox.
This newsletter may contain advertising, deals, or affiliate links. Subscribing to a newsletter indicates your consent to our Terms of Use and Privacy Policy. You may unsubscribe from the newsletters at any time.
Hits: 0